Introdution
Pluribus One WAS® is designed to complement the solutions already existing in the infrastructure, which thanks to Pluribus One WAS® can be leveraged to enable monitoring and protection of the Web Services. This is meant to relief the customer from the burden which generally arises from deploying a traditional Web Application Firewall in addition to the already existing Security and Traffic balancing components. Pluribus One WAS® works instead in parallel with the existing infrastructure, having thus no impact on that being then extremely easy to deploy.
Connecting Pluribus One WAS® to a Data Source
In order to deploy Pluribus One WAS® within an infrastructure, it is first necessary to identify a possible Data Source: we use the term Data Source to mean any component that receives the HTTP(s) traffic directed toward the Web Services and that can forward it or store it. Once Pluribus One WAS® is connected to a Data Source, it has the chance to observe the traffic toward the Web Services, monitoring thus their security. This allows it to run its detection modules on the traffic and thus to spot attacks being launched against the services.
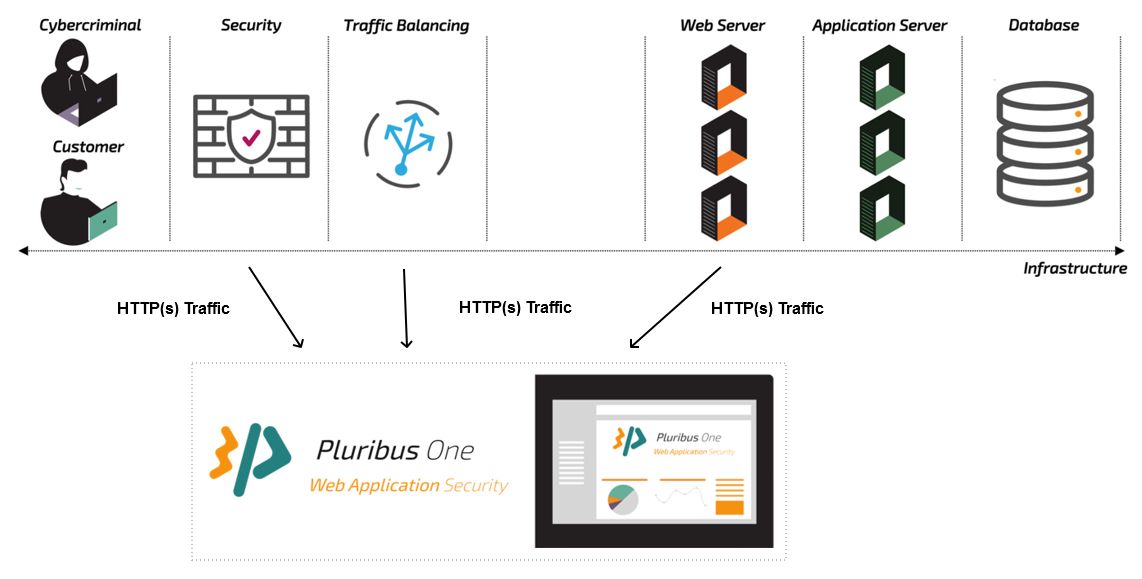
Pluribus One WAS® can read the incoming data traffic from several types of sources including:
- Web Servers.
- Traffic Balancing components such as Load Balancers, Reverse Proxies, Application Delivery Controllers.
- Security solutions such as Web Application Firewalls or Perimetral Firewalls.
Currently, Pluribus One WAS® already supports several free and commercial products of this kind. Also depending on the possibilities which each vendor has foreseen in its own product regarding exporting data externally, different ways of connecting Pluribus One WAS® to a Data Source may be possible. Generally speaking, such possibilities include:
- Syslogs - A specific syslog format is defined on the data source and it is sent to the Pluribus One WAS® host.
- Database - Some products are equipped with an internal database on which the network traffic is stored while flowing through the product. If access to the data stored in the database can be granted to external solutions, Pluribus One WAS® can read the traffic directly from it.
- Dedicated Connector - Using a dedicated Connector provided by Pluribus One, which is installed onto the same host where the Data Source virtual appliance is running.
- API - Many products make available an API to access the data. In such case, Pluribus One WAS® can leverage that API to use the product as a data source.
Using Pluribus One WAS® to implement Web Application Firewall mechanism.
The Pluribus One WAS® GUI features a guided procedure which, starting from the requests which have been spot as malicious, allows to define easily detection and protection rules through which Pluribus One WAS® can automatically react to the attacks against the monitored Web Services. From a technical standpoint, such policies translate into rules which are matched against the traffic. Generally speaking, whilst this will in practice implement a Web Application Firewall like protection mechanism, it does not require in practice a dedicated WAF to be present in the infrastructure. Any component which has the capability to inspect the traffic at the application layer and to import protection rules, can be in principle leveraged.
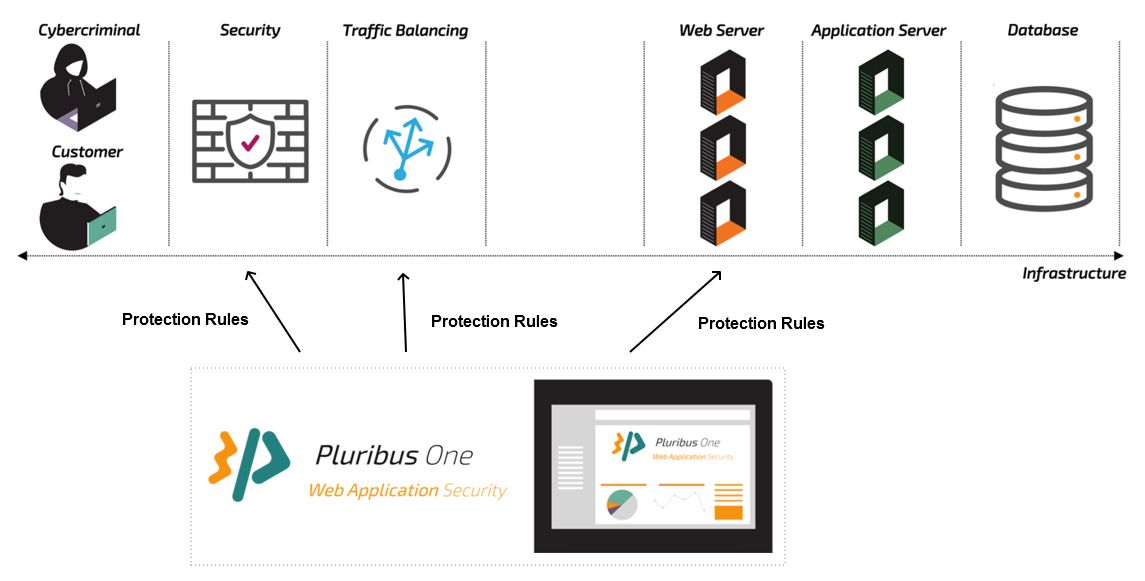
As shown in the picture above, such components generally include:
- Web Servers.
- Traffic Balancing components, like Load Balancers, Reverse Proxies, or Application Delivery Controllers.
- Security solutions, as perimetral Firewalls or Web Application Firewalls.
Currently, Pluribus One WAS® already supports several products of this kind including free and commercial ones.


